Creating and Configuring Permissions for Azure Credentials
We must create an Azure Service Principal to connect with the Microsoft Azure API.Creating an Azure Service Principal
To create a new Azure Service Principal, we need to open the Azure CLI or Azure Cloud Shell and run the following BASH command.This command also assigns the service principal a role and scopes that role assignment to our entire Azure subscription.
To access cost information, we might start with the "Reader" role, as it allows for reading most resources, including billing information, without the ability to make changes.
az ad sp create-for-rbac --name "kopicloud-dbx-cost" --role Reader --scopes /subscriptions/OurSubscriptionId
Note: We need to replace OurSubscriptionId with our Azure Subscription ID. To get the list of Azure Subscriptions, please type:
az account list --output table
And this is the result of the creation of the service principal:
guillermo [ ~ ]$ az ad sp create-for-rbac --name "kopicloud-dbx-cost" --role Reader --scopes /subscriptions/7980af11-c4ec-46d2-9797-68d69e76df71
Creating 'Reader' role assignment under scope '/subscriptions/7980af11-c4ec-46d2-9797-68d69e76df71'
The output includes credentials that you must protect. Be sure that you do not include these credentials in your code or check the credentials into your source control. For more information, see https://aka.ms/azadsp-cli
{
"appId": "6bc3536a-2929-4b23-ad48-b39cd6d1662b",
"displayName": "kopicloud-dbx-cost",
"password": "sxE8Q~su_Es47a.TFWt56uNr5kebEwsFO~J_LaBd",
"tenant": "6d94c202-cca8-48a9-ac66-d75af6930eaf"
}
Creating 'Reader' role assignment under scope '/subscriptions/7980af11-c4ec-46d2-9797-68d69e76df71'
The output includes credentials that you must protect. Be sure that you do not include these credentials in your code or check the credentials into your source control. For more information, see https://aka.ms/azadsp-cli
{
"appId": "6bc3536a-2929-4b23-ad48-b39cd6d1662b",
"displayName": "kopicloud-dbx-cost",
"password": "sxE8Q~su_Es47a.TFWt56uNr5kebEwsFO~J_LaBd",
"tenant": "6d94c202-cca8-48a9-ac66-d75af6930eaf"
}
Granting Access to Billing Information
The next step is granting access to the Billing Information.To access billing information, the service principal needs permission to read billing data.
This permission is not included in the "Reader" role by default and requires additional steps:
For Enterprise Agreement (EA) accounts, we need to have the Owner or Contributor role at the billing scope level.
We can set this through the Azure Portal under Cost Management + Billing.
In the left navigation pane, we click Billing scopes and select an Azure billing account.
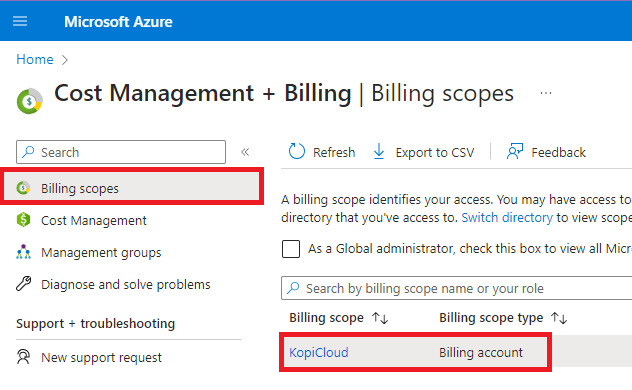
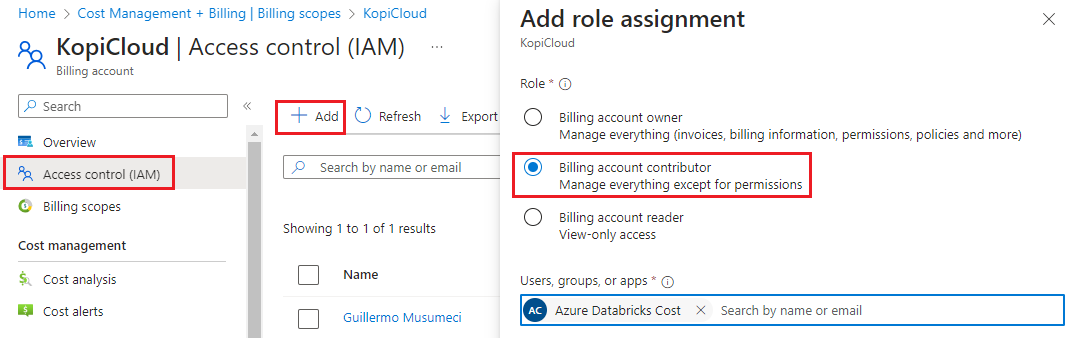
Then, we click Access control (IAM), and after click on the Add button (located on the top).
In the Add role assignment page, select the Billing account contributor role.
Finally, we type the name of the service principal created above and click the Add button.
Configuring the Azure Credentials in the KopiCloud Azure Databricks Cost tool
We click on the Configure Credentials menu to configure our Azure Subscriptions.
On the Azure Credentials tab, we must enter the Subscription ID, Tenant ID, Client ID (appId), and Client Secret (password) generated in the previous step.
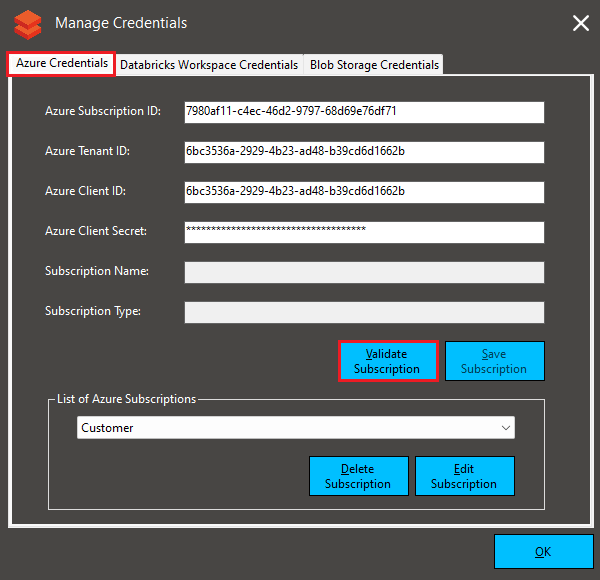
Then, we click on the Validate Subscription button.
If the information is corrected, the tool will retrieve and show the Subscription Name and Subscription Type.
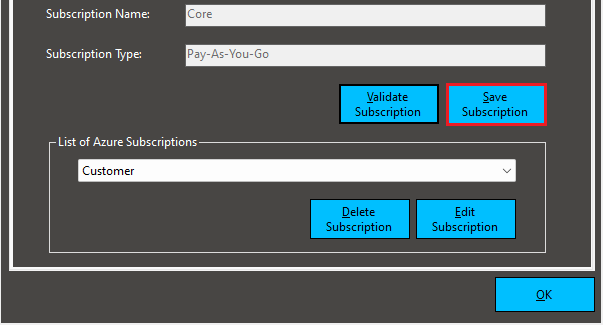
Finally, we click on the Save Subscription button to store the credential.
Important!
- For your security, the Azure credentials are stored securely on a local file.
- They are NOT transmitted or stored anywhere, and they are only used to call the Microsoft APIs.
- The credentials are encrypted and salted twice with the Advanced Encryption Standard (AES)-256 encryption algorithm.
Manage Azure Credentials in the KopiCloud Azure Databricks Cost tool
The KopiCloud Azure Databricks Cost tool supports multiple Azure Subscriptions.We can see the Azure Credentials in the List of Azure Subscriptions section:
If we need to delete an unused subscription, we must select the Azure Subscription from the drop-down and click the Delete Subscription button.
After confirmation, the subscription will be removed from the credential's file.
If we need to edit an Azure Subscriptions, we must select it from the drop-down and click the Edit Subscription button.
All the original subscription data can be edited. After the changes, we must validate and save the new subscription data.